We extremely advise taking the 8 courses On this certificate program while in the buy offered, since the information builds on info from before courses.
SocialPilot has emerged as Probably the most efficient social media hack tools. No matter what the dimensions of your small business, SocialPilot eases your marketing recreation by permitting you to attach as several social accounts as you want in your prospects in one position.
Clare Stouffer, a Gen worker, is often a writer and editor for the organization’s blogs. She handles different matters in cybersecurity. Editorial note: Our articles give academic info for you. Our offerings may not protect or defend against just about every sort of crime, fraud, or danger we compose about.
On the web courses on Coursera can introduce you to the fundamentals of cybersecurity, including various types of cyber threats and security tools.
কিভাবে কালিলিনাক্স ব্যাবহার করে এডভান্স ফিশিং অ্যাটাক করা হয়।
"If a thing even larger was at stake, such as the presidency, this might have seriously disastrous outcomes and undermine our democratic procedures."
Developing belief by fooling individuals into believing within the legitimacy of the Wrong character is among the major tenets of social hacking.
টিকটক অ্যাকাউন্ট গুলা কী ভাবে হ্যাক করা হয় এবং আমরা কী ভাবে টিকটক অ্যাকাউন্ট হ্যাকারদের থেকে নিরাপদে রাখতে পারি।
We know how to Find criminals and contact police of their abroad jurisdictions. We've aided Many individuals similar to you. So its your convert to choose Report On the web Blackmail or not
Khoros is really a marketing platform that companies can use to deal with their social media communications. Usually these platforms deal with or have use of the passwords and login aspects in their clients.
Normally Log off and become twice as scholastic with shared desktops. Don't share your password with Other individuals, In spite of your best friend or your superior 50 %. This is certainly non-public for just a reason and you need to by no means underestimate the chance that you choose to take when permitting some other person know your personal data.
The purpose of moral hacking is to test and shield see it here the security and knowledge methods of the Business an ethical hacker is Doing work for. Such a hacking is also called “penetration screening” because the white hat hacker, or moral hacker, checks the program to discover if you will find any regions to breach or exploit.
Hootsuite is the popular social media administration software that can help you track and manage all your social media profiles.
"When we ended up designed conscious of The problem, we locked the compromised accounts and they are working carefully with our associates at Facebook to restore them," Twitter claimed in a press release.
 Luke Perry Then & Now!
Luke Perry Then & Now! Anna Chlumsky Then & Now!
Anna Chlumsky Then & Now!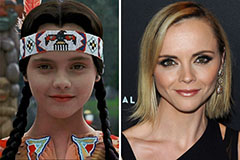 Christina Ricci Then & Now!
Christina Ricci Then & Now! Atticus Shaffer Then & Now!
Atticus Shaffer Then & Now! Robin McGraw Then & Now!
Robin McGraw Then & Now!